Analysis of the legislative framework
.
Adopted at the end of January 2016, the Law on Information Security was the first legislative document in this field, regulating standards of protection for information systems that private and public actors are now obligated to adopt. The Law defines the ICT systems of particular national importance as the systems used by state agencies, systems that process sensitive personal data, and those in industries and services of national interest. These activities also include electronic communication. It is crucial for information systems controlling the critical infrastructure to have an adequate level of protection prescribed by law, especially in the era of sophisticated technical attacks and a rapid development of cyber-weapons. Although online and civic media will not be found under the definition of ICT systems of special importance (except if they process particularly sensitive data), the respect of the principle of protection and implementation of measures prescribed by the Law and bylaws may crucially advance the level of information security of each subject.
The Government of Serbia adopted bylaws needed for the implementation of the Law on Information Security, setting the standards of necessary protection measures, content of the general act and actions to be taken in case of an incident, all of which completed the legislative framework for Operators of ICT systems of special importance. There are four regulations published in the Official Gazette of the Republic of Serbia as of 24 November 2016:
1. Regulation determining the content of the Security Act for information and communication systems of special importance, ways of verification and content of reports on security audits of information and communication systems of special importance;
2. Regulation determining the measures for protection of information and communication systems of special importance;
3. Regulation determining the list of activities in the fields in which activities of general interest are performed and in which information and communication systems of special importance are used;
4. Regulation on the procedure for data submission, lists, types and importance of incidents and importance of incidents and procedures of notification on incidents in information-communication systems of special importance.
The Law in Articles 14-19 defines and specifies the roles of:
– National CERT;
– Special CERT;
– CERT of the bodies of the Republic of Serbia and
– CERTs of independent ICT systems operators
On one hand, the legal system establishes the National CERT, the competence of which covers all the ICT systems in the Republic of Serbia and all the incidents and events jeopardizing the security of the ICT system. On the other hand, all other CERTs contribute to the prevention and protection against security risks in information systems within a particular area of business, companies, or groups of companies.
In line with the Law, a special CERT can be a legal entity or an organisational unit within a legal entity. This status is acquired by registering in the special CERTs registry based on the registration with the National CERT, i.e.RATEL. The very registration process is regulated by the Rulebook on special conditions for registration of special centres for the prevention of security risks in information-communication systems (Official Gazette of the Republic of Serbia, No. 12/17).
Criminal Code (Official Gazette of the Republic of Serbia, No. 85/2005, 88/2005 – corr., 107/2005 – corr., 72/2009, 111/2009, 121/2012, 104/2013, 108/2014) stipulates several criminal offences which may jeopardize online and civic media. The entire Chapter 27 of the Criminal Code refers to criminal offences against the security of computer data such as:
Article 298 of the Criminal Code states that whoever without authorisation deletes, alters, damages, conceals or otherwise makes unusable a computer datum or program, may be punished by fine or imprisonment up to one year. In addition, if the offence specified in paragraph 1 of the Article results in damages exceeding a certain amount, the offender may be punished by imprisonment of up to five years.
Article 301 of the Criminal Code stipulates that whoever enters incorrect data, fails to enter correct data or otherwise conceals or falsely represents data and thereby affects the results of electronic processing and transfer of data with intent to acquire for himself or another unlawful material gain and thus causes material damage to another person may be fined or punished by imprisonment of up to three years. Additionally, if this causes damage exceeding a certain amount, the offender may be punished by imprisonment of up to ten years.
Article 303 of the Criminal Code states that whoever without authorisation prevents or hinders access to a public computer network may be punished by fine or imprisonment up to one year. In addition, if the offence specified in paragraph 1 of this Article is committed by an official in discharge of duty, such official may be punished by imprisonment up to three years.
Article 304 of the Criminal Code stipulates that whoever uses computer services or computer networks with intent to acquire unlawful material gain for themselves or another, may be punished by fine or imprisonment up to three months.
In addition, the following articles of the Criminal Code are important, too:
Article 146 of the Criminal Code states that whoever without authorisation obtains, communicates to another or otherwise uses information that is collected, processed and used in accordance with law, for purposes other than those for which they are intended may be punished with a fine or imprisonment up to one year. In addition, if the offence is committed by an official in discharge of duty, such person may be punished with imprisonment up to three years.
Article 138 of the Criminal Code states that whoever endangers the safety of another by threat of attack against the life or body of such person or a person close to him may be punished with fine or imprisonment up to one year. Additionally, whoever commits the offence specified in paragraph 1 of the Article against several persons or if the act has caused disturbance of the general public or other serious consequences, may be punished with imprisonment of up to three years.
The Law on Authority and Organisation of State Entities for Fight against High-tech Crime (Official Gazette of RS, No. 61/2005, and 104/2009) for the first time defined the competent bodies for the fight against cyber-crime. A Special Office of the Prosecutor for High Technology Crime was established within the Public Prosecution Office in Belgrade and it is in charge of criminal prosecution of high-tech crime committers whereas the proceedings occur before the High Court in Belgrade.
In line with Article 9 of the Law, the Department for Fight against High-Tech Crime was established in 2007, as a part of the Service for Fight against Organised Crimes of the Ministry of Interior of the Republic of Serbia. This Department acts on the request of the Special Prosecutor for the Fights against High-Tech Crime, whereas the Minister of Interior based on the expert opinion of the Special Prosecutor appoints and dismisses the chief of the Service and determines the work of this Department more closely.
(The organisational structure was taken over from the website of the Ministry of Interior: http://www.mup.gov.rs/cms_lat/UKP.nsf/sbpok.h?OpenPage)
The above mentioned bodies are in charge of discovering, criminal prosecuting and conducting proceedings for criminal acts against the security of computer data determined by the Criminal Code in Articles 298-304a:
· Damaging Computer Data and Programs
· Computer Sabotage
· Creating and Introducing of Computer Viruses
· Computer Fraud
· Unauthorised Access to Computer, Computer Network or Electronic Data Processing
· Preventing or Restricting Access to Public Computer Network
· Unauthorised Use of Computer of Computer Network
· Manufacture, Procurement, and Provision to Others of Means of Committing Criminal Offences against Security of Computer Data
These bodies are in charge of other criminal acts, too, which due to the object and means or manner of their conducting may be considered criminal acts of high-tech crime such as criminal acts against copyrights or property when computers or computer systems are used to conduct such acts.
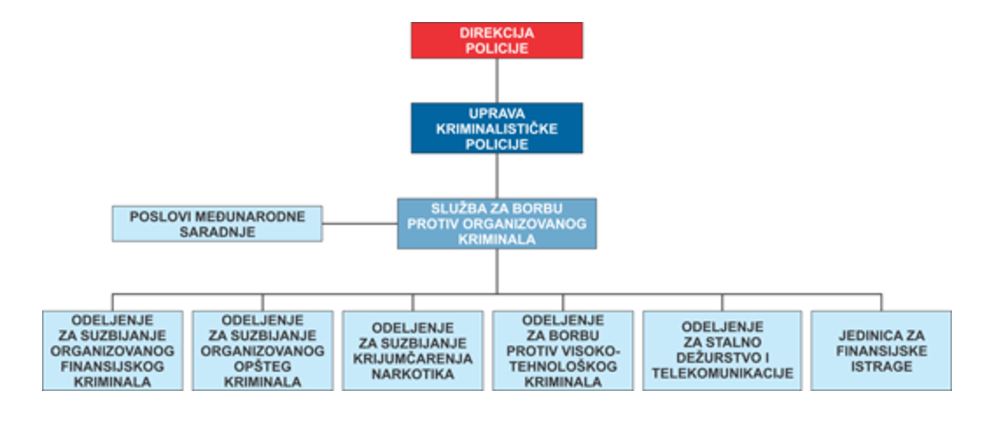 (Organizaciona struktura je preuzeta sa sa web prezentacije Ministarstva unutrašnjih poslova: http://www.mup.gov.rs/cms_lat/UKP.nsf/sbpok.h?OpenPage
(Organizaciona struktura je preuzeta sa sa web prezentacije Ministarstva unutrašnjih poslova: http://www.mup.gov.rs/cms_lat/UKP.nsf/sbpok.h?OpenPage
